What is Zero Trust Network Access, and Does Your Business Need One?
August 4th, 2022 | 4 min. read

Even with COVID-19 receding into the distance, it will be hard to go back to the old ways.
Gone are the days when workers were required to go to the office daily and attend in-person meetings to be considered good employees. They have now realized that they can be as productive or even more working remotely.
And as a business owner, you must embrace this change. Furthermore, you have to accommodate situations and scenarios wherein people will have to use their personal computers and mobile devices, given that the company cannot provide everything.
However, that’s not all there is to it, you must also recalibrate your remote security since networks have now become more complicated and dispersed.
Zero Trust Network Access or ZTNA plays into that. It creates perimeter-less security that enables remote users to access internal applications securely.
But unlike the traditional client Virtual Private Network or VPN, which allows users to connect to the local network freely, ZTNA, as the name suggests, is more distrustful in nature.
As a Managed IT Service Provider with a key focus on cybersecurity, ITS helps hundreds of businesses strengthen their network defenses by incorporating rigorous access controls across the distributed network so that the IT infrastructure remains protected.
Here, we’ll go over the following key points:
- What is ZTNA?
- How does ZTNA work?
- Who needs ZTNA?
- What are the benefits of ZTNA?
And by the end of this article, you will have a deeper understanding of ZTNA and why you should consider integrating it into your system.
Firstly, what is Zero Trust Network Access?

ZTNA is the modern version of remote access VPN. To help you differentiate the two, Edward Griffin, a Partner at ITS, gave a brief distinction:
“Remote access VPN is a means for staff working remotely to establish a secure tunnel from your local network computer to the office network. By default, when you’re connected to that VPN, you're going to have full access to the entire network. This could be problematic.”
Because employees are accessing the business network from unsecured places, such as cafés, libraries, and even at home, they’re basically putting the entire set of network infrastructure at risk. And if the remote user’s connection is compromised in some fashion, the attackers will have the opportunity to access all the assets in the network.
An alternative to that is something that’s been developing for several years but has only been exclusive to the military, government, and big enterprises due to the cost. It's only now starting to trickle down the medium business market– the Zero Trust configuration.
ZTNA is an evolution that allows the remote workforce to access corporate applications but not necessarily the network.
“You wouldn’t want that flat access to an entire network like a traditional VPN. But rather, very targeted pinpoint access to a specific application or content source. ZTNA does exactly that.”
It identifies the system that needs to be accessed remotely, the network assets, and the roles and privileges to allow the end users just the right point of access. Technically, it should align with the three principles of least privilege: availability, integrity, and confidentiality.
“You have to assume that everything out there can be breached. Therefore nothing can be trusted.” Griffin adds.
Another thing you should know is that contrary to a VPN, where one will remain connected and trusted the entire time the session is active, ZTNA will repeatedly challenge all users' identities, not just at the initial connection time but all throughout the session.
How does ZTNA work?
Here is a brief description of the process:
Firstly, users must be authenticated to the ZTNA service. Then, ZTNA grants the user access to specific applications on a one-to-one basis through a secure, encrypted tunnel. This tunnel offers an extra layer of security protection by masking applications and services from IP addresses. Without the IP, attackers will have a hard time locating and infiltrating the connection and the device.
Thus, implementing ZTNA across the organization protects not just the office network but all the devices connected to it.
Who needs ZTNA?
From a security standpoint, every business will need ZTNA in due course.
“We recommend it to everyone who needs something to manage the risks, ourselves included.” Griffin says.
But in the short term, Griffin mentions that ZTNA will be more relevant to clients with a regulatory compliance burden. These are institutions like healthcare, where HIPAA governance is present, or financial services institutions where banking information is stored.
All in all, institutions that hold sensitive data that is regulated according to a certain industry and for which a breach might incur predefined and severe penalties will benefit the most from ZTNA.
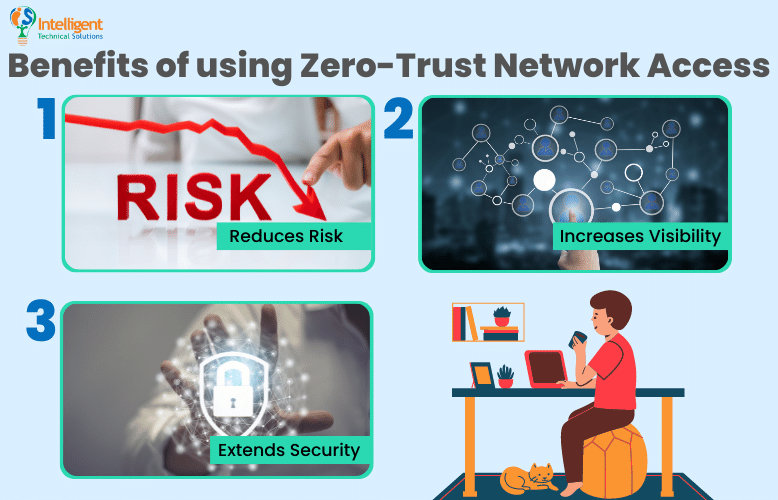
What are the benefits of using ZTNA?
There are a lot of benefits that go along with ZTNA. Fortinet lists down these top three advantages:
1. Reduces risk
When you automatically extend trust to any device or user in your network, you put your organization at risk when either becomes compromised, whether intentionally or unintentionally.
Zero trust eliminates points of vulnerability by limiting network access for users and by adopting extensive identity verification so that they only have access to the data and systems relevant to their role or position in the organization.
2. Increases visibility
Apart from the obvious security benefits, having ZTNA allows you to know who and what is connected to the network at all times.
3. Extends security
Security can be extended beyond the network with ZTNA. Unlike a VPN, which focuses exclusively on the network layer, ZTNA goes up a notch, effectively providing application security independent of the network.
Need help implementing Zero Trust Network Access?
In today’s cybersecurity landscape, where perimeters have become blurry, if not gone, businesses will need more than the traditional solutions to protect their network. ZTNA is one of the many technologies you can count on.
Still, as much as you’d want your business to level up your cybersecurity maturity, at ITS, we understand how complex the steps are to get there. We’re here to help.
If you’re planning to implement ZTNA in your network, the first thing you must do is improve your IT infrastructure. Download and read this e-book to know the three types of cybersecurity solutions small businesses must have.
Jess is a Content Writer who commits herself to creating helpful, relevant, and easy-to-digest technical articles. When she isn't writing, she devotes her energy (and money) to collecting K-Pop photo cards, which she likes to call an 'investment.'
Topics:
