Uncover Your Business's Vulnerabilities with Penetration Testing
June 8th, 2022 | 5 min. read

Doesn't it feel that cybercriminals are always two steps ahead? Year after year, the number of cybercrime incidents continues to rise at an alarming rate. At this point, you either know someone whose business has been attacked recently, or you yourself have experienced it firsthand.
In fact, Check Point's study on 2021 cyberattacks discovered that the corporate networks experienced a 50% increase in attacks per week. The situation worsened as the year came to its conclusion. In the final quarter, organizations had to endure up to 900 attacks weekly.
To make matters worse, the COVID-19 pandemic and worldwide shift to remote work setup created bigger gaps in the already vulnerable network security of businesses.
-1.png?width=778&name=Smaller%20Blog%20Template%20(5)-1.png)
So, why do cyberattacks continue to rise despite modern security programs? The answer is simple. Cybercriminals have learned to adapt to the evolving landscape of cyberspace. Instead of mounting a head-on attack on cyber defenses, criminals now look for backdoor entrances in your defense system to infiltrate your network.
Like hunters hunting for prey, hackers study their targets and look for vulnerabilities first. Once discovered, they devise the most efficient way to exploit them. And when the right time comes, they attack swiftly taking all that's worth taking.
Now wouldn't it be nice if you could find out the weakness of your cybersecurity before criminals do? It's like finding a hole in your fort before a massive attack- a discovery that saved you from a significant dilemma and costly expense.
What if I tell you, it's possible? Sounds dreamy, doesn't it? Well, it's not. A service that can help you uncover the faults in your cyber-defense before hackers do actually exist, and it's called Penetration Testing or Pen Tests.
At Intelligent Technical Solutions (ITS), we help hundreds of businesses protect their networks with advanced cybersecurity solutions. In this article, we'll discuss what Penetration Testing is about and how it's conducted. More importantly, we'll tell you how Pen Tests can help improve your cyber defenses.
What is a Penetration Test?
Penetration testing is the intentional launching of simulated cyberattacks on an IT network. Its goal is to test the robustness of an organization's security policy. These tests are conducted by ethical hackers mimicking the strategies of a hacker for a realistic simulation of the attack.
Studies of this nature are vital in ensuring strong cybersecurity of a business. It allows them to find vulnerabilities in their system before attackers exploit them.
The insights gathered from Pen Tests help businesses find solutions to the vulnerabilities of their network and fine-tune their security policies.
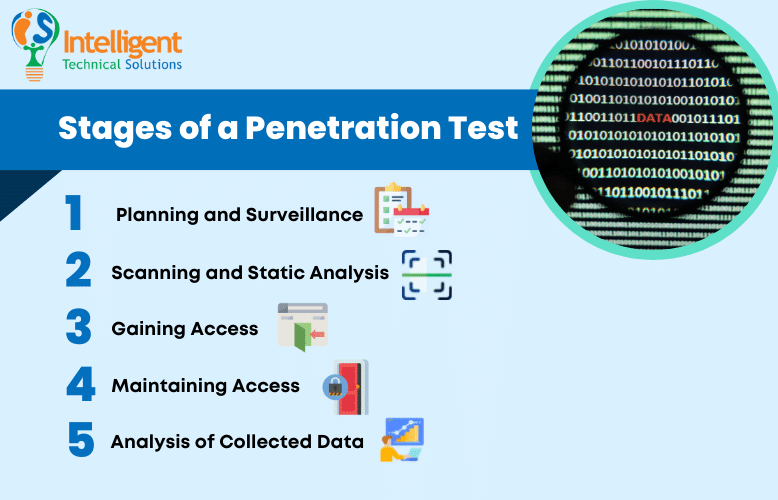
What are the Stages of a Penetration Test?
Penetration Testing is divided into five different stages. Each phase is crucial in assessing the vulnerabilities of your network. The following are the steps involved in conducting penetration tests:
1. Planning and Surveillance
The first step is setting the goals and gathering the necessary data. This step outlines the systems and testing methods to be addressed during the test. Like real attackers, test conductors will also study the subject to assess their plan of attack.
2. Scanning and Static Analysis
This step is about understanding how the subject's defense responds to infiltration attempts. It is orchestrated using the following methods:
- Static analysis – Inspects an application's code to estimate its behavior while running. This process scans an entire code in a single pass.
- Dynamic analysis – Inspects an application's code in a running state. It provides a real-time view of an application's performance which is more practical compared to the Static method
3. Gaining Access
The third phase includes gaining access to a network using web application attacks. It is where ethical hackers try to uncover as many vulnerabilities as they can in your network. The tester exploits these openings by escalating privileges, intercepting traffic, and stealing data to understand the damage they cause.
4. Maintaining Access
The stage determines if the vulnerability can provide hackers with a long-term presence on the subject's network. The notion is to replicate how advanced persistent threats sit in a network for months to continuously mine data.
5. Analysis of Collected Data
The final stage is where testers create and present their report. Typically, the report would specify the following:
- Vulnerabilities exploited
- The types of data accessed
- Duration the attackers remain undetected while in the system.
These data will be submitted to the IT team to help them patch their vulnerabilities and create a more robust security measure.
Benefits of Penetration Test
Penetration tests do great in finding vulnerabilities in your network. It allows your business to work on the gaps in your defense measures before cybercriminals discover them. But it's not the only benefit your business will get when implemented. The following are other advantages your company can gain from Penetration Testing.
 Prevent Costly Data Breach Expenses
Prevent Costly Data Breach Expenses
Dealing with cyberattacks and their aftermath is expensive. Halted production, legal fees, drop in sales, and customer trust will cost you thousands to millions of dollars. Plus, the road to recovery is not a simple path. It takes a significant time and lots of money to recover what you lost. You'll also have to shed more as you try to win back your customer's confidence.
 It Will Help You Allocate Your Security Budget
It Will Help You Allocate Your Security Budget
A Penetration Test will tell you about the areas in your cybersecurity that need improvement and those that don't. Having such information will help you better allocate your budget. Instead of blindly spending upgrades on programs that are already effective, you can allow it on an area that's in dire need of enhancement.
It will also help you realize if the size of your current IT team is sufficient for your needs or not.
 It Keeps Your Defense Measures Compliant with the Industry Standards
It Keeps Your Defense Measures Compliant with the Industry Standards
Penetration Tests adhere to security and compliance requirements set by industry regulations and standards, including Payment Card Industry Data Security Standard (PCI), Federal Information Security Management Act (FISMA), Health Insurance Portability and Accountability Act (HIPAA), and ISO 27001.
Subjecting your cyber-defense programs to a Pen Test means measuring their effectiveness based on the requirements set by your state and security-specialized organizations. It will also help your team understand the standards in the cybersecurity field.
 It's an Authentic Way to Test Your Cybersecurity Measures
It's an Authentic Way to Test Your Cybersecurity Measures
Since penetration tests simulate actual attacks, conducting one in your network will identify if your defense program is indeed effective against hackers. Moreover, it will give your team an idea of how attacks work and what they need to do to prevent them from getting worse.
 Strengthens Customer Trust
Strengthens Customer Trust
Publishing a press release on your Pen Test result can build your credibility and boost customer trust. It will give the impression that your business is serious about improving your cybersecurity, especially when the result is positive.
Negative results can also be leveraged to your benefit. After working on its improvement, you may publish the negative result and the things you've done to remediate the issues.
Is Your Business Willing to Undergo Penetration Testing?
If you are dead serious about strengthening your business's cyber defense, then taking up a penetration test has got to be on your to-do list.
It will help you identify the gaps in your defense that you're not aware of. If you are too confident in what you have, you are putting your business, employees, and customers at serious risk.
With penetration tests, you'll be able to save up by spending only on areas that need improvement. It will also help our business achieve an industry-standard defense measure. Most of all, it will prevent cyber breaches and all the dilemmas that come with it.
As cybercriminals find new ways to infiltrate your network, your efforts to patch up your vulnerabilities should do the same.
At ITS, we are committed to helping you make smart IT decisions for your business. This means providing you with the necessary information and tools your employee needs for an efficient and productive team.
Serious about improving your defensive measures? Download and read our eBook 3 Types of Cyber Security Solutions Your Business Must Have to learn more!
Topics:
