Top 3 Security Risks of Bring-Your-Own-Device (BYOD) Policy
July 5th, 2023 | 4 min. read
%20(77)-1.jpg)
Editor's note: This post was originally published on February 14, 2018 and has been revised for clarity and comprehensiveness.
Bring-Your-Own-Device or BYOD policies not only gave employees the liberty to work using their own devices from home, cafés, or anywhere they wish. It also helped businesses grow by saving money and increasing productivity.
However, despite all the conveniences of the BYOD Policy in the remote work landscape, it comes with several risks that can negatively impact a business.
At Intelligent Technical Solutions (ITS), we have years of experience helping hundreds of businesses create a secure IT environment by providing solutions fit for their unique needs. We released this article to answer the following questions:
- What is BYOD?
- What are the risks of BYOD?
- How can businesses reduce the risks of BYOD?
By the end of this article, you will know how to secure all your devices while reaping the benefits of BYOD.
What is BYOD?
BYOD, or Bring Your Own Device, is a policy that allows employees to use their personal devices for work purposes. This approach has become increasingly popular during the height of the pandemic as it enables employees to work from anywhere, at any time, using devices they are most comfortable with.
However, using personal devices for work brings certain security and privacy risks that must be addressed through a clear and concise BYOD policy.
What are the security risks of BYOD?
Whether set up as a formal policy or adopted during the height of the pandemic, BYOD can pose threats to your business. And as an organization, you need to be aware of these risks to implement the best practices to mitigate them.
.png?width=1280&name=Blog%20Image%20Template%20(3).png)
These are three of the most common risks of BYOD you should know:
1. Lack of control over devices
When employees use their own devices, it can be difficult for the company to ensure they are not downloading or installing malicious software or other harmful applications. This can put the company's sensitive data and systems at risk.
If an employee's personal device is lost or stolen, the company may be unable to retrieve sensitive data stored on it. When this happens, quickly send a report to your IT team so they can immediately block remote access.
2. Vulnerability to cyberattacks
Personal devices may not have the same level of security as company-owned devices, and employees may not be aware of the importance of protecting sensitive company information.
Your organization probably already has anti-virus programs on remote desktops to protect users from cyberattacks. But what about your employees’ mobile devices, tablets, and other equipment? Since most people are bound to connect all their devices for convenience and accessibility, it wouldn’t be hard for hackers to see that as a potential gateway and target those as well.
Employees may also connect to public networks and then check emails. Doing this gives hackers a chance to intercept the traffic coming to and from their devices and then use it to infiltrate your company’s systems, thus causing data breaches.
In the event of a security breach, sensitive information such as trade secrets, customer data, and financial information can fall into the wrong hands. This can result in major financial losses, damage to the company's reputation, and even legal consequences.
3. Legal implications of a data breach
If employees are storing sensitive company information on their personal devices, it can be difficult to ensure that the data is properly protected in accordance with applicable laws and regulations.
For example, companies may be required to comply with regulations such as the EU General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), which imposes specific requirements on the storage and protection of personal data.
How can businesses reduce the security risks of BYOD?
A well-planned BYOD policy goes a long way in minimizing the risks of a remote work setup. For your business to thrive while keeping your data safe, here are the recommended BYOD best practices you can implement in your organization:
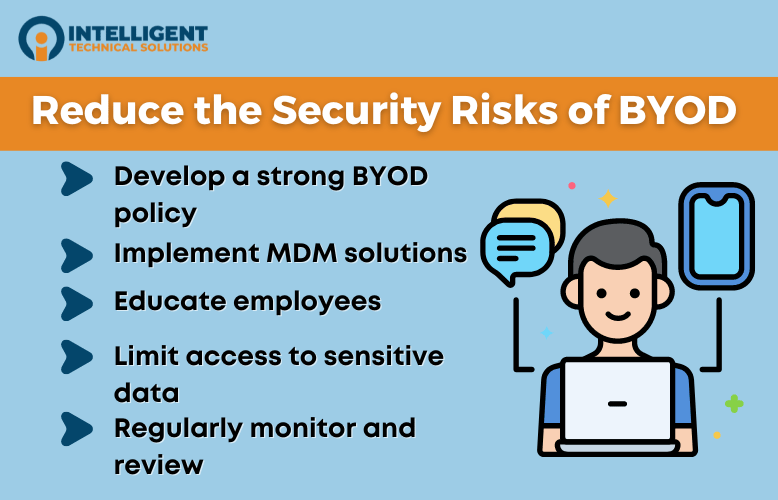
1. Develop a strong BYOD policy
A clear and concise BYOD policy is essential in reducing the risks associated with BYOD. The policy should outline the specific devices and operating systems that are supported, security measures that must be in place, and procedures for remote wiping of company data.
2. Implement mobile device management (MDM) solutions.
MDM solutions can ensure that all devices used for work purposes are secure. This includes measures such as password protection, encryption, and anti-virus software.
3. Educate employees.
Employees should be made aware of their responsibilities when using their devices for work purposes, including the proper handling of sensitive information and reporting of any security incidents.
Remember to regularly educate employees on the dangers of malware, phishing scams, and other security threats.
4. Limit access to sensitive data.
Limiting access to only those who need it is essential to reduce the risk of compromised sensitive data. You can achieve this through user authentication and the implementation of access controls.
4. Regularly monitor and review.
Regular monitoring and reviewing of the BYOD policy and security measures are critical to ensure they are effective and current. This includes:
- Regularly testing the security measures in place,
- Monitoring for security incidents, and
- Updating the BYOD policy as needed.
Ready to enforce a secure BYOD policy in your company?

While BYOD can bring many benefits to the workplace, it is vital to know and reduce the risks associated with it by:
- Developing a strong BYOD policy,
- Implementing MDM solutions,
- Educating employees,
- Limiting access to sensitive data, and
- Regularly monitoring and reviewing.
Implementing these practices allows organizations to ensure that their data and systems remain secure.
At ITS, we enforce strong security controls that separate end users' work and personal data. We accomplish this by deploying an MDM program and implementing stringent BYOD policies for our employees' and clients' IT environments.
Learn more about BYOD and cybersecurity by reading these free resources:
- How to Set Up a Secure BYOD Policy on a Windows Environment
- 5 Things Every Business Owner Needs to Know to Protect Against Cyberattacks
- 3 Types of Cybersecurity Solutions Your Business Must Have
- What Businesses Need to Know About Managed Cybersecurity Services
If you have any more questions about implementing a BYOD policy or MDM program for your organization, you may also talk to one of our client support representatives for assistance.
Jess is a Content Writer who commits herself to creating helpful, relevant, and easy-to-digest technical articles. When she isn't writing, she devotes her energy (and money) to collecting K-Pop photo cards, which she likes to call an 'investment.'
Topics:
