What is Software Supply Chain Attack? (& How to Protect Your Business)
August 19th, 2022 | 5 min. read
%20(33).jpg)
In a bid to maximize damage and profits, hackers have expanded their target groups. They’ve set their sights on B2B (Business to Business) companies instead of solely focusing on end-users. Bad-faith actors are hoping to catch a big business off-guard and exploit all the data underneath a company’s umbrella of connections.
And while everyone should be wary of cybercriminals, the pressure is on businesses to drastically up their cybersecurity game.
These threats, aptly named software supply chain attacks, can unexpectedly bring companies to their knees in one fell swoop. As a Managed IT Service Provider, we’re aware of the danger of supply chain attacks and their possible effects on our clients.
You need to be prepared to defend your business against these kinds of attacks and deserve to know if you are at risk – whether you’re a booming retailer or an avid customer.
So, we’ll discuss:
- What is a software supply chain attack?
- What kinds of businesses are vulnerable to it?
- How can supply chain attacks affect you?
- How can you protect yourself from supply chain attacks?
After a complete read-through, you should be able to identify the steps you need to take to protect your company.
What is a Software Supply Chain Attack?
A software supply chain attack is a type of cyber threat where a hacker compromises a customer’s data or system by infecting legitimate applications they use.
An attacker looks for unsecured network protocols or unprotected server infrastructures to infiltrate a software vendor’s network. Once in, they will infect the vendor’s application by changing sourcing codes and hiding malware in their build and update processes.
The software will then act as a trojan horse for the malware without the vendors realizing it. Since the virus is embedded in the app, it will run on customer devices with the same permission as the app it is rooted in.
Hackers get a two-for-one deal, with the software creators and customers compromised in a web that may take months to untangle.
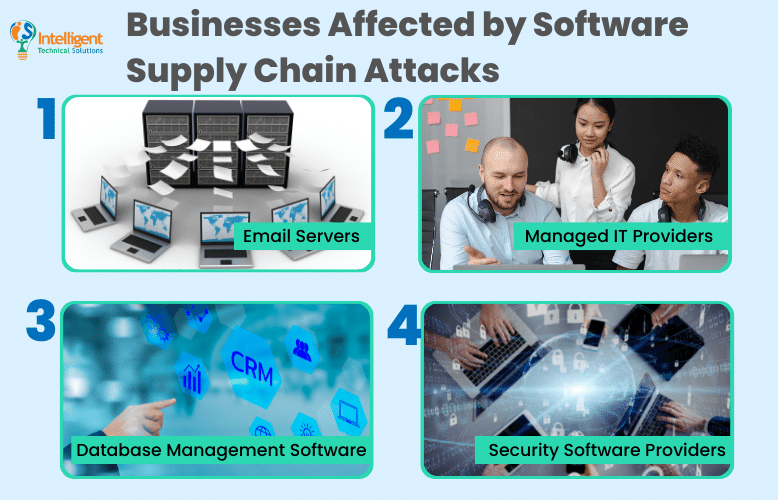
What Businesses are Affected by Software Supply Chain Attacks?
Some of their commonly targeted applications and businesses are:
- Email Servers
- Managed IT Providers
- Database Management Software
- Security Software Providers
Email Services
All cloud services – particularly email services – are appealing targets for supply chain attacks. If hackers get access through these programs, they’ll have access to almost all your information and data. Also, almost everyone who uses the internet to conduct business transactions has email & cloud services, resulting in a wider pool of victims for cyber criminals.
Even the FBI isn’t safe from supply chain attacks. In November last year, multiple emails from their email servers were sent out, attempting to discredit Vinny Troia (head of security research of the dark web intelligence companies NightLion and Shadowbyte).
If the FBI itself was a victim, you could be too.
Managed IT Providers
In supply chain attacks, hackers target upstream vendors like Managed IT Service Providers (MSPs) to increase their victim count. Attacking MSPs allows damage to cascade down the supply chain to another supplier – a consequence sometimes known as the “waterfall effect” – which increases collateral damage against many targets.
Hackers also know that compromising updates from trusted vendors allow them to bypass security measures and infect all users that install them.
For example, REvil ransomware infected over a thousand companies after targeting a few MSPs last year. All eight of the affected MSPs are using Kaseya VSA.
Database Management Software
Databases are a goldmine of information, as their entire function is to store data for you. When your database, whether on-premises or cloud-based, is a victim of a supply chain attack, you’ll have to treat that as leaked data and take immediate action.
Security Software Providers
What better way to attack multiple companies than to sneak in via security software? Consumers and businesses rely on security software and trust third parties to keep their IT system safe. By using security software as a trojan horse, hackers can stay in systems for a long time before they’re discovered.
How Can Supply Chain Attacks Affect You?
First and foremost, ask yourself: where are you along the supply chain? Are you an end-user, B2C (Business to Customer) company, or B2B (Business to Business) supplier? The effects of a supply chain attack will look vastly different based on what kind of user you are.
You’re an End-user (Customer)
If any of your software is compromised, then all the data you’ve allowed that software to collect is compromised too. You will need to immediately take steps to mitigate the damage to your network and work on removing all traces of the infected software from your system.
Depending on how you used the infected software, you may need to retire passwords, usernames, and email addresses to regain a secure network.
You’re a Software Creator (Company Owner)
Whether your business deals directly with consumers (B2C) or with other businesses (B2B), if you create or manage software and are infected by a supply chain attack – you’ve effectively funneled all your and your client’s data to cyber criminals.
You will urgently have to:
- Evaluate your network
- Inform customers of a data breach
- Send out patches fixing the issue
- Re-establish trust with your customers
- Pay any compliance fines
How Can You Stop Supply Chain Attacks?
So, how can you avoid experiencing the headaches that come with supply chain attacks?
Whether as a client or as a CEO, you can use the following tips and tricks to prevent software supply chain attacks.
1. Ask Each Business a Set of Security Questions

During the Right of Boom security conference last February 2022, President and CISO of F1 Solutions Jennifer VanderWier listed ten security questions you need to ask your software suppliers to ensure the safety and security of your client. They are:
- Have you assessed your tool? Against what standard?
- Do you have a remediation plan with timelines you can meet?
- Has your product ever been breached?
- Is multi-factor authentication (MFA) an option for your tool?
- Can you access our client’s data? What controls are in place? And do you have a shared responsibility matrix in place that you can share with me?
- What protections are in place to protect your code?
- How many people are on your security team?
- What are your limits of liability?
- In what ways can I limit vendor access to sensitive data?
- Do you have a disaster recovery plan, and when was it tested?
As a software provider, you can also use this list to evaluate yourself and build confidence in your security systems.
2. Conduct Frequent Security Awareness Training
Increasing security awareness among employees is a critical step in stopping attacks. But even if you’re not running a business, you’ll benefit from keeping up with the latest cybersecurity news.
3. Conduct Penetration Testing

Penetration testing is ethical hacking that tests the defense capabilities of an organization. It simulates a real-life cyberattack to discover weaknesses in a company’s defenses. This method allows you to identify a fault in your defenses and work on it before hackers find them.
As a customer, you’ll want to ask your software and security providers if they conduct tests like these on their systems.
4. Proactive System Scanning
Proactive system scanning helps you identify problems in your network early on – either as a client or a business. Issues and attacks can be dealt with immediately and resolved before they become a severe threat to you.
5. Install Software Updates

Zero-day vulnerabilities play a vital role in the spread of supply chain infections. Closing those gaps will reduce potential damage to your business and IT network. Moreover, it can stop the attack before it even happens.
6. Deploy a Multi-Layered Cybersecurity Defense
Some supply chain attacks find their way into your network by piggybacking on a software update. Multi-layered network security can stop this by blocking communication with known-malicious IP addresses.
Are You Prepared to Stop Software Supply Chain Attacks?
A software supply chain attack infects a legitimate application to distribute malware. It infiltrates a software provider's network and infects its applications. Like a trojan horse, the attack starts after the application has been installed on your or your client’s network or device.
Software supply chain attacks are devastating and can affect your credibility and safety. Managed IT companies like ITS rely on our client's trust in us to keep the company thriving, and we know how crucial it is to keep businesses from losing credibility.
If conducting all these tips and tricks on top of maintaining the day-to-day functionality of your business seems daunting, you may want to get a professional IT management company to handle your IT department. Learn about Managed IT by reading our content: Everything You Need to Know About Managed IT.
Kharmela Mindanao is a senior content writer for Intelligent Technical Solutions. She’s called Ella by her friends and likes yoga, literature, and mountain climbing. Her favorite book is Anxious People by Fredrik Backman. She creates art and poetry and is on a quest to find the best cheesecake.
Topics:
