4 Major Cyberthreats That Business Owners Should Be Aware Of
May 19th, 2022 | 3 min. read
Are you concerned with your cybersecurity? You should be. It’s times like this that you need to gather up all your defenses and put them up to protect your business from the increasing risks in the cybersecurity landscape.
As far as cyber risks go, the previous year recorded a massive 50% surge in cyber-attacks per week on corporate networks compared to 2020. That’s 925 cyber-attacks per week per organization, or five attacks per hour to put that into perspective. 43% of affected companies are small business owners.
With all that, 2022 is expecting an even higher risk percentage. If you don’t have a strong defense against these threats, your business may not survive. However, in order to protect yourself, it is critical to understand what the risk is and how it will affect your business.
At ITS, we’ve helped hundreds of businesses strengthen their cybersecurity posture by managing their technology. In this article, we’ll go into a bit of a refresher and brush up on the basics of cybersecurity, specifically the four major cyber threats that you should be aware of. Also, expect a few notes on what you can do to avoid it.
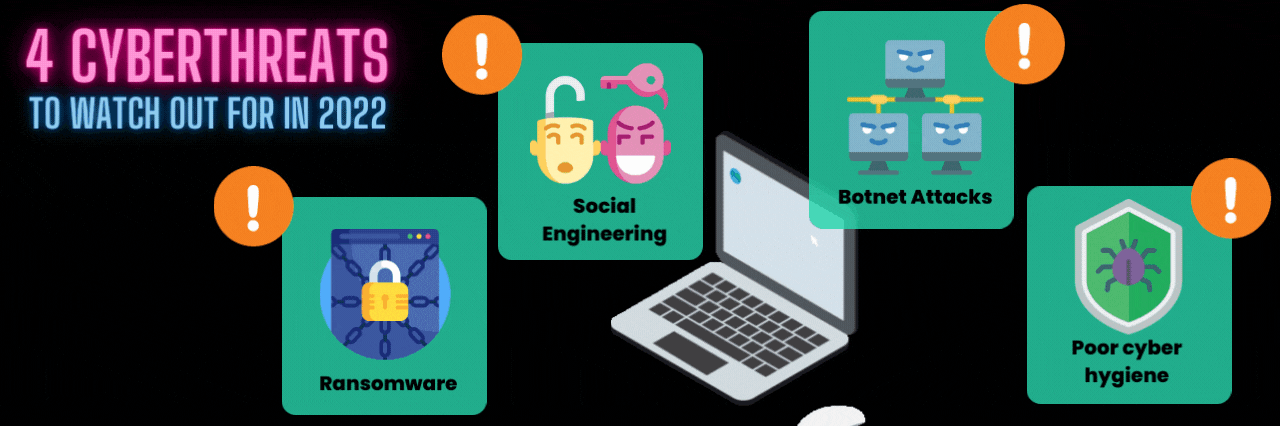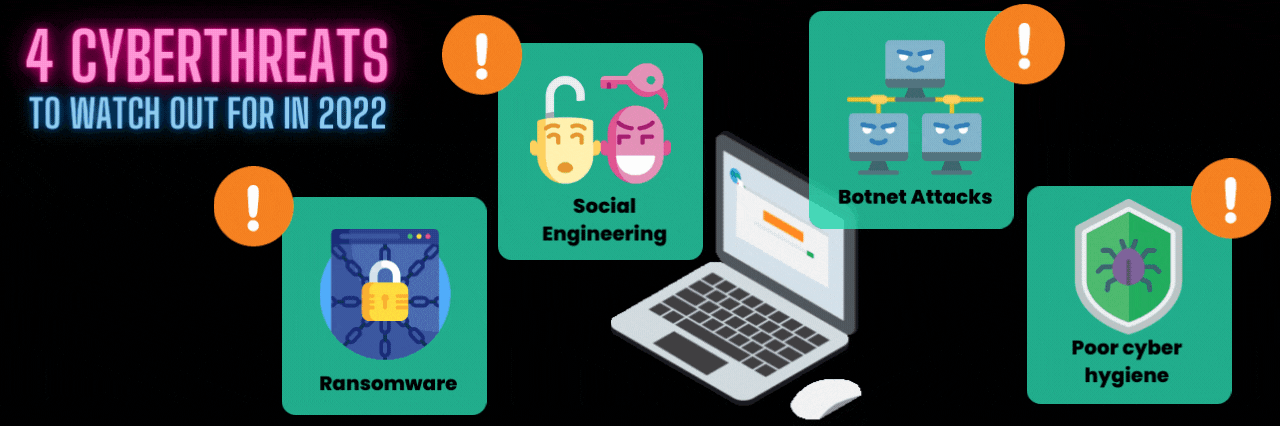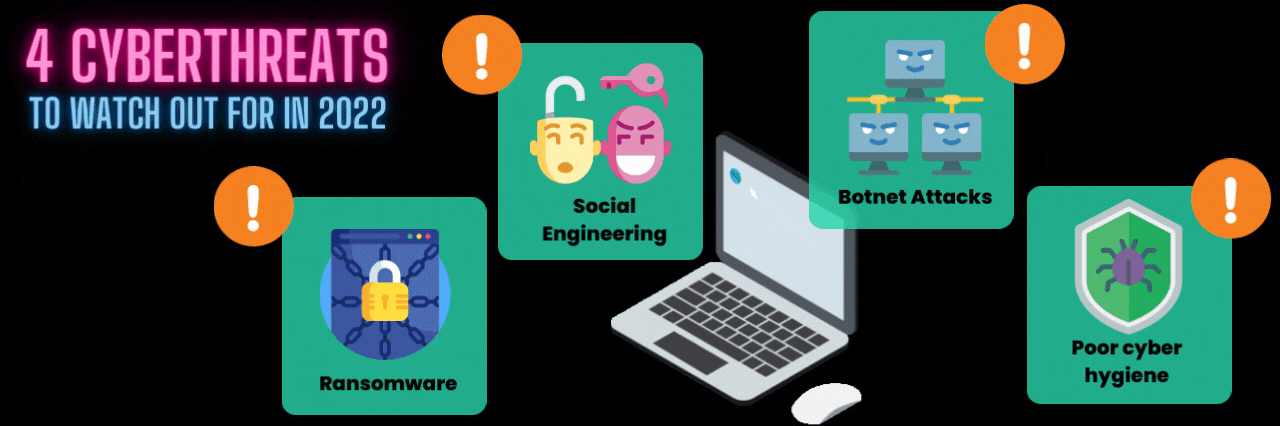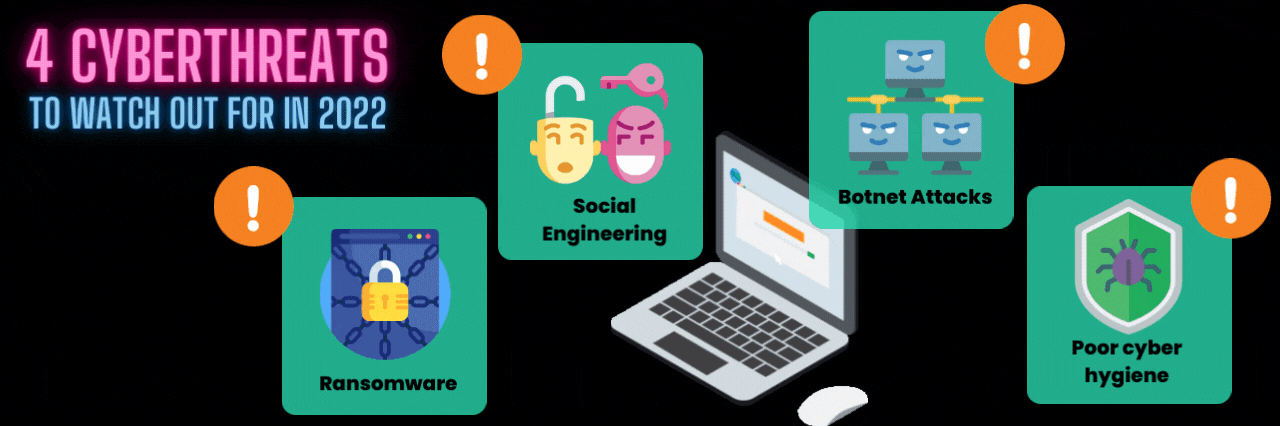
4 Cyberthreats to Watch Out For in 2022
There are plenty of cyber threats out there. But we’ll stick to the biggies.
 1. Ransomware
1. Ransomware
Undoubtedly, ransomware is one of the fastest-growing cybercrimes out there. The International Data Corporation (IDC) tallied approximately 37% of ransomware victims globally in their 2021 Ransomware Study.
Ransomware is when some evil entity plants malicious software on your computer that encrypts all your files–photos, music, documents, databases–you name it! Then, once they get hold of your important files, these cybercriminals will hold it all hostage until you buck up and pay up the ransom.
How does it happen?
Often, it’s an innocent, alluring email attachment you or someone at your organization unknowingly opens and downloads. And all of a sudden, your computer is infected. Worse, it may spread out to the entire network. With all the systems down, the hacker will present a ransom amount to be paid in the form of Bitcoin or the like.
However, paying the ransom does not guarantee total data recovery. As reported by Sophos, on average, only 65% of encrypted data is recovered after the ransom was paid.
 2. Social engineering attacks
2. Social engineering attacks
Social engineering is a broad-ranging type of cyber deception that aims to trick people into giving out their personal information. You may think you can spot this threat one mile away, but not the good ones. Social engineers are slick, masters at their trade, and know what makes people click.
There are various approaches linked to social engineering, one common type is phishing. It is an approach that casts a widespread trap across thousands of individuals with no specific target. Generally, it works by sending out malicious emails to unsuspecting targets. Once the receiver clicks on a link within the said email, it will go downhill from there.
So, what should you watch out for to avoid getting preyed on by phishers?
Forgeries
Avoid emails that are made to look like they’re from a trusted source or sender. Such could look like a delivery notice for FedEx, a due bill payment, or a storage quota alert.
Stay alert, and do not take the bait! Look for misspellings in the sender’s address and the body of the email. Additionally, not quite right graphics are also a dead giveaway.
Spear phishing
This is a more targeted form of phishing, which monitors your online behavior and activities to know what you’re currently interested in.
These cyber attackers are apt to bait you by referencing a conference you’ve recently attended, a topic you’ve searched for, or a site you’ve visited. Don’t let them trick you into clicking these links.
Like what has been mentioned in the previous paragraphs, be observant.
Whaling attacks
These attacks are much like spear-phishing, but the difference is while spear phishing goes after a category of individuals with a lower profile, whaling attacks target the high-ranking individuals–CFOs, CEOs, and government officials–who hold valuable company data and industry trade secrets.
Whaling attacks come in the form of emails regarding critical business issues or potential clients. It may take months to execute and will require extensive research skills to be able to reach the executives. But once it does, it will cause huge damage to the organization.
 3. Botnet attacks
3. Botnet attacks
According to Spamhaus Botnet Threat Update, the fourth quarter of 2021 has seen a 23% rise in the number of new botnet command and control (C&C) attacks.
If you’re not familiar with a botnet, these are a network or group of devices on the same network that is on a mission to burrow into and take control of your computer brains. It infiltrates and infects the entire business network with malicious code and malware and turns the chosen device into a brainless zombie bot that the attackers can control.
 4. Poor cyber hygiene
4. Poor cyber hygiene
Without proper cyber hygiene, you are preparing your business for a disaster. The consequences may include data loss, operational downtime, and reputational damage, which will lead to financial loss.
Start prioritizing your cyber hygiene if you don’t want this to happen.
Here is a quick list of things you can do now:
- Conduct a regular data cleanup
- Update software
- Update old passwords
- Incorporate multi-factor authentication (MFA) across all devices
- Back up data
- Create a disaster recovery (DR) plan
By following these tips, you can mitigate the potential risk and damage and strengthen your cybersecurity posture.
Need help protecting your business from cyber threats?
Unfortunately, due to today’s ever-changing technology, there will probably be no absolute state of cybersecurity unless you’ve gone off the grid completely. But we can take precautions.
If you want to gain a more detailed understanding of what it takes to protect your business from every angle, read this e-book.
Jess is a Content Writer who commits herself to creating helpful, relevant, and easy-to-digest technical articles. When she isn't writing, she devotes her energy (and money) to collecting K-Pop photo cards, which she likes to call an 'investment.'
Topics:
