How to Be Proactive (Not Reactive) with Your Cybersecurity
September 23rd, 2022 | 4 min. read
No company is 100% safe from cyberattacks.
Regardless of its size, your organization is a target for hackers. If you do not have a strong defense, you might soon need to spend enormous resources on data recovery, compliance regulatory fines, and ransom demands.
Now, when setting up cybersecurity strategies, you can be reactive or proactive.
The traditional reactive approach mitigates cybersecurity incidents without much foresight. In contrast, a proactive approach means taking steps, even before an incident occurs, to prevent and significantly reduce the impact of cyberattacks.
Between the two strategies, a proactive cybersecurity approach is more critical than ever. Here’s why.
We consistently hear about the increasing number of exploits, malware, ransomware, and other cybercrimes that disrupt business activities. We are sadly in a time where it is no longer a matter of if but when a security incident will hit you. From this perspective, a reactive model will raise the risk of malicious hackers infiltrating your network. With a proactive approach, you can patch vulnerabilities before hackers discover them, stay on top of emerging threats, and avoid severe consequences.
At Intelligent Technical Solutions (ITS), we have helped businesses across varying industries proactively manage their IT security. In this article, we will review the most crucial steps and practices that make for a robust and proactive IT security strategy.
6 Tips to Implement a Proactive Approach to Cybersecurity
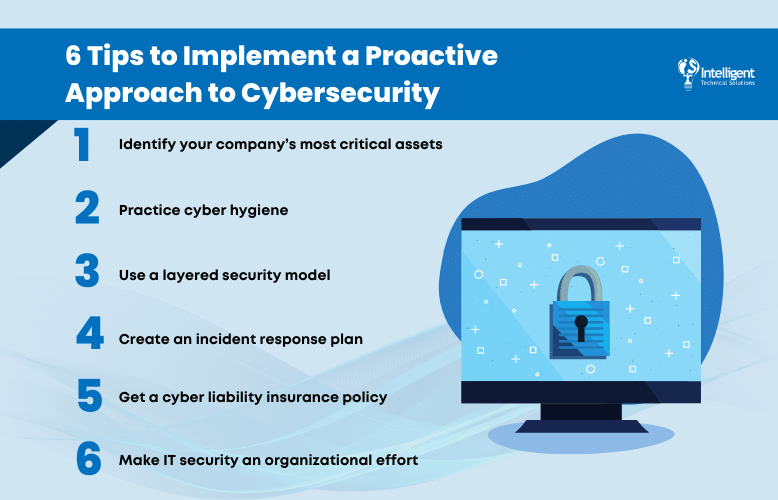
1. Identify your company’s most critical assets
Proactive cybersecurity starts with identifying your company’s most important data assets. These include customer, employee, and financial data. Knowing the data that can negatively impact your processes, bottom line, and reputation is critical when your company gets hacked or compromised. Once identified, you can set up appropriate safeguards and create an effective risk management program.
In addition to your company’s digital assets, paying attention to your physical premises is essential. Ensuring proper physical security further minimizes risks.
2. Practice cyber hygiene
When it comes to creating an effective cybersecurity security strategy, there’s no silver bullet. It takes consistency to remain vigilant and keep your company safe from disasters. Because the simplest threats can cause significant damage, practicing good cyber hygiene is a must. Some of the procedures that you should be making a habit of are:
- Using a variety of strong, complex passwords for different applications, systems, and services
- Monitoring, reviewing, and updating processes and systems
- Scanning your networks to look for holes and vulnerabilities and resolving them immediately
- Conducting backups and testing your backups
- Checking for network vulnerabilities and performing the latest security patching
- Updating security firmware and applications for firewalls, networks, and devices
- Reviewing policies or guidelines for data breach prevention and detection
- Performing penetration testing to check your defenses and identify any gaps

3. Use a layered security model
Many data breaches have occurred because companies have been lax with their cybersecurity, creating easy pickings for hackers. The doors were too easy for them to open. To make things harder for hackers, set up a layered security model.
There are quite a few things to put in place to create a solid layer of security. One of the most important is multi-factor authentication. This method strengthens the security of your applications and systems by keeping unauthorized users at bay. Other security measures to reduce risk include phishing protection and spam filtering solutions. This help prevents malicious suspicious content from getting into your inbox or network. Of course, having up-to-date firewall technology is also needed to block threats.
4. Create an incident response plan
A 2018 IBM report found that 77% of companies do not have an existing incident response plan. That means many businesses will encounter a chaotic environment in the event of a significant security breach.
To reiterate the importance of an incident response plan, we asked Rob Schenk, a partner here at ITS. Rob mentions that an incident response plan is a critical playbook on how a business would respond after a security incident. When it happens, most companies often don’t know what to do, where to ask for help, or whom to talk to. The delays waste a lot of time and escalate the level of negative impact and severity.
Having a written and documented response plan ahead of time is essential so you are prepared to respond to a cyberattack. Do not forget that testing your plan is necessary as well. Make sure it is assessed, refined, and validated to match your organization’s security needs on a recurring interval.
5. Get a cyber liability insurance policy
Comprehensive cyber liability insurance is a critical part of an ongoing security program. It gives you peace of mind because it covers forensic investigations, litigation expenses, and regulatory fines that may incur after a breach.
Before applying for insurance, ensure your cybersecurity measures are up to the latest standards. Talk with your MSP about the minimum requirements you need to meet to get a policy and choose the right provider.
6. Make IT security an organizational effort
Cybersecurity should not only be the responsibility of the IT department but the goal of every member of your company. This is where security policies and awareness training come in. You want to ensure your employees take security seriously. You want them to be aware and follow the necessary IT security measures to be safe online at work.
You can promote a culture of proactive cybersecurity when the initiative comes from the leadership team. According to Schenk, “Companies that have ingrained their security program in their culture and whose executives are leading by example have the most success with their cybersecurity programs.”
Ready to implement these proactive IT security measures?
As hackers find creative and more sophisticated ways to attack, taking a proactive, forward-thinking approach to your cybersecurity is necessary. Your entire organization must embrace an offensive security mindset to protect assets and your reputation. Implementing these steps can save you from the devastating effects of a breach:
- Analyze the risks by identifying your most crucial data
- Practice good cyber-hygiene consistently
- Set up layers of security across all applications, websites, and web solutions
- Develop a written and documented incident response plan
- Get a cyber liability insurance policy
- Promote a culture of cybersecurity within the organization
At ITS, we understand that strengthening your security measures can be overwhelming. It is difficult to deploy a perfect cyber security system all in one go. As an MSP, we are here to assist you in improving your security one step at a time. Download our FREE cybersecurity checklist to help you create a comprehensive plan for protecting your business against attacks.
Kriselle Paladin started her career as a content writer in 2014. Since then, she has eagerly explored various types of online writing and produced blogs, social media campaigns, travel articles, and product reviews. Outside writing, Kriselle spends her time playing with her dogs and doing volunteer work.
Topics:
