Who are These Cyber Gangs and What are They Up To?
June 6th, 2022 | 4 min. read
%20(4)-4.png)
When we think about cyberattacks, we often presume a lone individual carries it out. Though that presumption might be true, most of us don't realize that hackers can also attack in groups.
These groups of thugs called cyber gangs to wreak havoc in a synchronized manner, allowing them to maximize damage in a single blow. Worse, they can eradicate cyber defenses by executing different attack scenarios simultaneously.
These groups have increasingly become a significant threat to businesses. They can disrupt your operations and extort money, leaving your team bankrupt.
At Intelligent Technical Solutions (ITS), we help hundreds of businesses protect their assets from cyber gangs by providing extensive security services. We’re also committed to helping companies make smart decisions on their IT needs by sharing valuable information about the technological marketplace..
This article will help you understand what a cyber gang is. It will also provide details on how they work and tips on what you can do to fend them off.
Who Are These Cyber Gangs?
.png?width=778&name=Smaller%20Blog%20Template%20(4).png)
Cyber gangs are very much real. Like the mob, they are a group of thugs banded together with a shared goal of profiting from the torment of others. They strike as a team, with each member doing their specific role for efficiency and maximum damage.
These groups plan their attacks wisely, and they choose their targets carefully. Unlike lone attackers, cyber gangs can take down many layers of defense in as little time as possible. Their diverse skill sets allow them to strike any business they want with little hassle.
Like the branches of the armed forces, each crew specializes in a specific vector of attack, and they also have their preferred type of target.
Cyber gangs generally fall into three categories which are the following:
- Nation-State Sponsored threat actors – Not all cyber gangs work for money. Some of them work with the government for national and international significance. Unlike regular hackers, these people never take ownership of their work. Nationalism is what fuels them in their drive. These groups typically use Advanced Persistent Threat (APT) to infiltrate their target networks.
- Financially Motivated groups (FINs) – As their name suggests, these groups are out for money. They target big corporations that can pay a large sum of cash for held data. These gangs rely primarily on phishing emails, working patiently to steal valuable information for months.
- Uncategorized groups (UNCs) – This group includes the general multitude of cyber gangs that were not included in the abovementioned.
What Consists a Cyber Gang?
Cyber gangs function like a special forces unit. They have a commanding officer that calls the shots, specialists, recon, and many more. They operate in sync with each member doing specific tasks based on their proficiencies.
The crew of a cyber gang may vary from one group to another, but the common positions include the following:
- Team Leader – The head of the group who calls the shots in the operation.
- Coders – They develop the necessary programs in launching the attacks. E.g., malware, spyware, ransomware, etc.
- Network Administrators – They are responsible for taking over an organization's online services or devices.
- Intrusion Specialist – They ensure the malware/spyware/ransomware remains on the network or device of their target.
- Data Miner – The person who can identify the valuable data/information and extract that data in a usable and clean format.
- Money Specialist – The contact that determines the most appropriate way to make money from various data types.
How Do They Operate?
Cyber gangs indeed have their way of executing their scheme. It can be a combination of different tactics or one vector refined by its member. You must become aware of their attack vectors to know where to focus your resources.
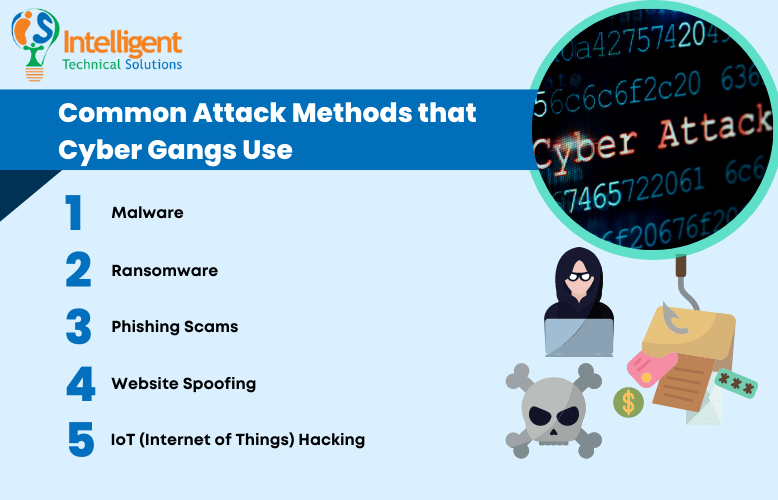
Here are the most common attack methods that cyber gangs use:
- Malware – Malware is the most widespread cyberattack that criminals use. It's malicious software installed on a network without the owner's consent. Depending on the type, its attack capabilities can range from gathering confidential data to monitoring the actions of its target and controlling computers.
- Ransomware – Ransomware is a form of malware that encrypt files, rendering them unusable. Attackers use it to hold a victim's information in exchange for a hefty ransom. Small and medium-sized enterprises are among the recent targets this type of attack.
- Phishing Scams – This cyberattack uses social engineering to trick its prey into giving away valuable information. Hackers disguise themselves as representative of a reputable organization, reaching out through email to offer help in stopping a bogus threat. But their true goal is to steal sensitive data or install malware on your network.
- Website Spoofing – It is a scam where hackers create a fraudulent website that mimics a known company. It tricks the company's customers and employees into sharing sensitive information like login credentials, banking info, etc. Cyber gangs fondly use them because they're easy to execute and very effective.
- IOT (Internet of Things) Hacking – IoTs are all devices capable of connecting to the web. It can range from mobile gadgets to smartwatches and even home security devices. Hackers target IOTs due to their vulnerability and the large volume of data that can be stolen. Mobile devices are attackers' favorite targets since they contain hundreds of valuable data like credit card details, credentials, etc.
Malware is the front runner when it comes to cyber gang activity. FireEye even noted that 514 new malware strains were developed and deployed in 2020. Of the strains developed, 81% were privately developed and had restricted availability. The remaining 19% were readily available strains.
Is Your Business Prepared for Cyber Gang Attacks?
Cyber gangs are a significant threat to your business. They can strike hard and fast and can leave your business incapacitated.
Prevent possible attacks by strengthening your defenses against their most common attack vectors. Raising cyber awareness in your team will also help increase your security.
If your budget allows, consider hiring a seasoned Managed IT Service Provider (MSP). An experienced MSP knows how to put up robust security measures that keep out cyber gangs for good. Besides, they can provide other benefits like proactive systems checks and IT help.
At ITS, we help hundreds of businesses create a strong cyber defense using the latest IT tech. We are also committed to helping businesses understand technology through our awareness articles.
If you want to learn more about how you can better defend your business, we suggest reading our article 14 Cyber Hygiene Tips to Keep Your Business in Tip-top Shape.
Topics:
