Colonial Pipeline Ransomware Attack: What Can You Learn From It
May 26th, 2022 | 3 min. read
%20-%202024-08-08T034253.680.jpg)
Ransomware has evolved significantly since CryptoLocker in 2013.
The early waves of ransomware were largely untargeted, opportunistic attacks, where attackers sent out spam emails with malicious attachments to thousands of users, hoping to get anyone to slip into the trap. The creators of CryptoLocker earned more than $3 million before the Department of Justice declared victory over the virus in 2014.
Since then, criminals have shifted their focus to more targeted attacks that provide higher payouts.
One recent incident that made headlines in 2021 was the Colonial Pipeline Ransomware Attack. Through an exposed Virtual Private Network (VPN) password, the attackers were able to infiltrate the network and steal 100 GB of sensitive data within a two-hour window. The attackers then infected Colonial’s IT network with ransomware that put the entire organization in shambles, consequently causing panic among people who depend on Colonial Pipeline for gas supply.
So, how did Colonial Pipeline overcome the attack, and what can you learn from this? Most especially, how can you ensure that the same thing doesn’t happen to your business?
At ITS, we’ve helped hundreds of businesses bolster their cybersecurity to prevent severe ransomware damage. In this article, we’ll delve into the following key points:
- A quick rundown on the Colonial Pipeline Ransomware Attack incident
- What can your business learn from the attack
A quick rundown on the Colonial Pipeline Ransomware Attack incident
On May 7, 2021, Colonial Pipeline fell victim to ransomware. After the hackers encrypted the business network, Colonial shut down its operational technology (OT) network as a protective step.
However, this caused oil to stop flowing through the largest refined petroleum products pipeline in the United States. As a result of the shutdown, panic buying arose, leading to gas shortages across the southern and eastern United States.
With the massive damage at hand, Colonial called in a well-respected third-party incident responder to assist with recovery efforts. Together, they worked to eliminate the presence of criminals from their network and restore data from backups. According to reports, Colonial Pipeline also paid approximately $5 million in ransom to the attackers. On May 12th, they resumed operations.
In the aftermath of this attack, President Biden signed an executive order to mandate increased controls for all federal agencies and IT service providers that contract with the federal government. It also increased reporting requirements for those doing business with the federal government.
What can your business learn from the attack?
Some business owners often believe that only large enterprises such as Colonial Pipeline are prone to ransomware attacks. False. Because you’re a revenue-generating business, you are a target.
In fact, according to Sophos, 37% of organizations were hit by ransomware in 2021. And one-third of that number are small to medium-sized businesses (SMBs). This just goes to show that cyber attackers take on every opportunity as long as there’s profit.
Colonial Pipeline was fortunate to have several backups that made data recovery easier since there were indications the decryption tool was slow and ineffective. If not, there would’ve been a greater loss. But it wasn’t all luck. In preparation for the worst-case scenario, they created an incident response plan to help reduce the risk of successful ransomware attacks and allow for more rapid recovery when one occurs–which they did.
That’s something you can apply to your business as well. Here we list down the things you can do to prepare your business for cyberattacks such as ransomware. The following list is a good starting point, although not as comprehensive.
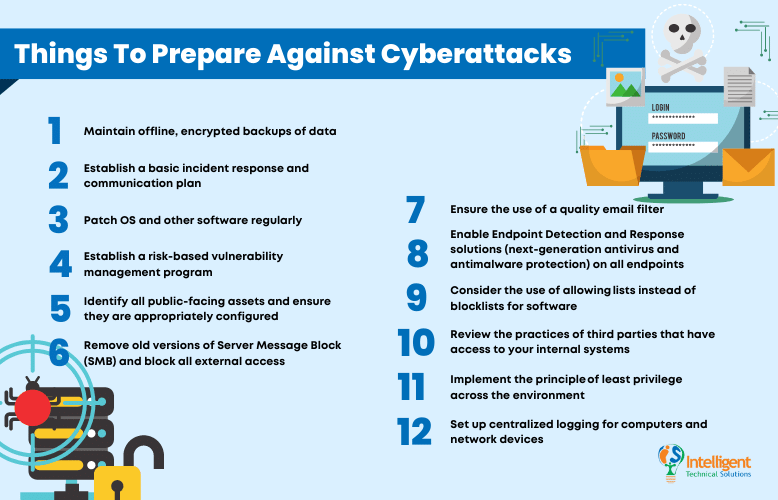
1. Maintain offline, encrypted backups of data
Regularly test these backups to ensure that they are valid and meet the defined recovery point and recovery time objectives.
2. Establish a basic incident response and communication plan
As mentioned above, make sure to review and practice the plans regularly to ensure effectiveness in times of trouble.
3. Patch OS and other software regularly
4. Establish a risk-based vulnerability management program
Follow these steps:
- Run regular vulnerability scans to identify vulnerabilities
- Classify the vulnerabilities
- Prioritize the vulnerabilities
- Remediate and mitigate the vulnerabilities
5. Identify all public-facing assets and ensure they are appropriately configured
- In addition to that, do not publicly expose services unless necessary, for example, RDP, SQL, the management interface for HVAC systems, etc.,
- Regularly patch all publicly exposed assets,
- And require multifactor authentication (MFA).
6. Remove old versions of Server Message Block (SMB) and block all external access
7. Ensure the use of a quality email filter
8. Enable Endpoint Detection and Response solutions (next-generation antivirus and antimalware protection) on all endpoints
9. Consider the use of allowing lists instead of blocklists for software
10. Review the practices of third parties that have access to your internal systems
MSPs and third parties are common attack vectors.
11. Implement the principle of least privilege across the environment
Restrict PowerShell and Group Policy access to only administrators.
12. Set up centralized logging for computers and network devices
SIEM (Security Incident Event Monitoring) products can help with log storage, correlation, and analysis.
Taking the above steps will significantly improve the security posture of your organization and can reduce the likelihood of a successful ransomware attack. However, there is no panacea. When your organization has a breach, it is important to implement the incident response plans as quickly as possible.
For more guidance and information, please review the MS-ISAC Ransomware Guide.
Prepare your business for ransomware attacks
Ransomware is an international scourge, and we need coordinated action to address it.
Fortunately, the need for collective action is being recognized–the Ransomware Task Force recently published a framework for combatting ransomware, and the Biden Administration is trying to address security shortcomings within the federal government. However, the steps will take time to implement and many of them will require continued international cooperation.
Until then, you can do your part to reduce the risk. Review the recommendations to mitigate the threat of ransomware, make sure you have a realistic incident response plan, and drill that plan.
Here at ITS, we help clients create a secure environment for their businesses. If you want to know the best practices you can do against ransomware, download this e-book.
Jess is a Content Writer who commits herself to creating helpful, relevant, and easy-to-digest technical articles. When she isn't writing, she devotes her energy (and money) to collecting K-Pop photo cards, which she likes to call an 'investment.'
Topics:
