Brain Hacking: How Hackers Use Your Brain Against You
July 20th, 2023 | 4 min. read

From security awareness training sessions to regular email reminders, you feel like you’ve done everything to keep your team informed of cyber threats. And yet, for some reason, members of your team are still slipping up and falling for scams and social engineering tricks. Does that sound familiar?
It happens way too often and is frustrating, especially for IT guys. However, hear us out before pinning the blame on gullible team members because the real insider threat might be much closer than you think. In fact, the culprit could be sitting right inside your head. That’s because hackers have developed ways of using your brain against you.
Intelligent Technical Solutions (ITS) is a managed security service provider (MSSP) with years of experience helping countless businesses bolster their cybersecurity efforts. In this article, we’ll explain what tricks cybercriminals use to hack into your mind. After reading, you’ll be armed with the knowledge to spot and avoid those tricks.
How Hackers Use Your Brain Against You
There is one mind trick that hackers love to use to get inside a person’s head, and that’s by exploiting your cognitive bias.
A cognitive bias refers to your brain’s tendency to simplify information processing by running it through a filter based on your personal experiences and preferences. That process is a coping mechanism to help you deal with large amounts of information quickly. Unfortunately, that’s also what hackers are looking to exploit.

Cognitive Bias Cheat Sheet by Buster Benson
To help you get a better understanding, let’s run through some of the most common ways hackers use cognitive bias to get past your defenses:
Loss Aversion
Imagine receiving $100 in your bank account - then someone takes it away. That pain hits harder than not having that money in the first place. That is what psychologists call loss aversion. In other words, the pain of losing something hurts twice as much as the pleasure of receiving it.
That feeling is something hackers like to exploit by offering you something nice and then threatening to take it away from you unless you do what they ask. In the context of this article, they might ask you to download something, send them your information, or click on a malicious link. Those are the hallmarks of a phishing scam.
What it Looks Like in Action:
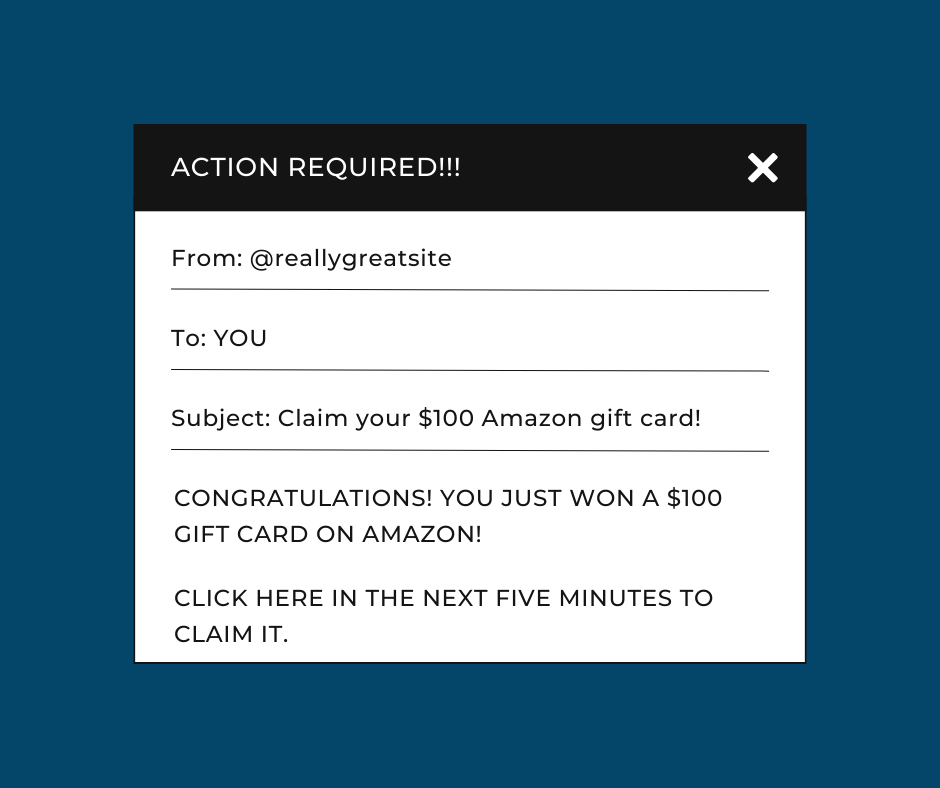
Urgency Bias
It’s incredibly difficult to make rational decisions in a panic. That’s how hackers use our urgency bias to get past your defenses. They will use everything at their disposal, such as pretending to be someone who has authority over you and create scenarios that will induce you to panic. From there, you are more likely to give in to demands without thinking twice.
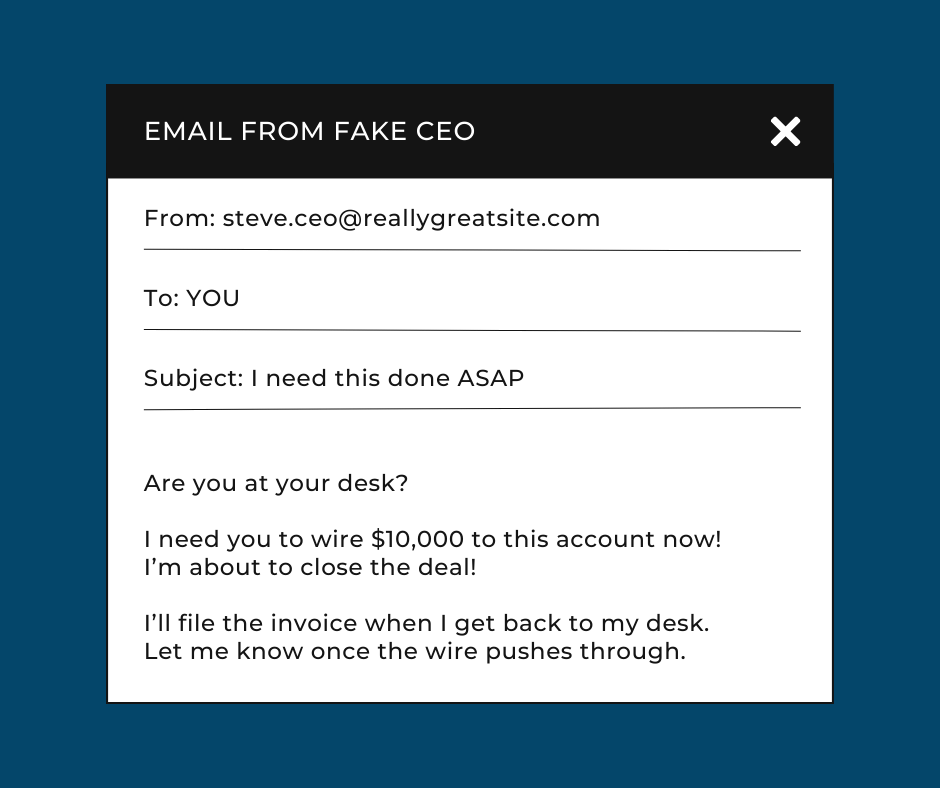
What it Looks Like in Action:
(Email from someone pretending to be the CEO of your company)
Fear Bias
Fear is one of our primal instincts that has helped keep humanity alive. But it’s also a major vulnerability. Fear is a potent persuader, and hackers know how to utilize it against you. They can reach out to you and create scenarios that will scare you into doing what they ask. However, it’s important to note that fear doesn’t always refer to fear of bodily harm or injury. It could also refer to the fear of losing your livelihood or assets.
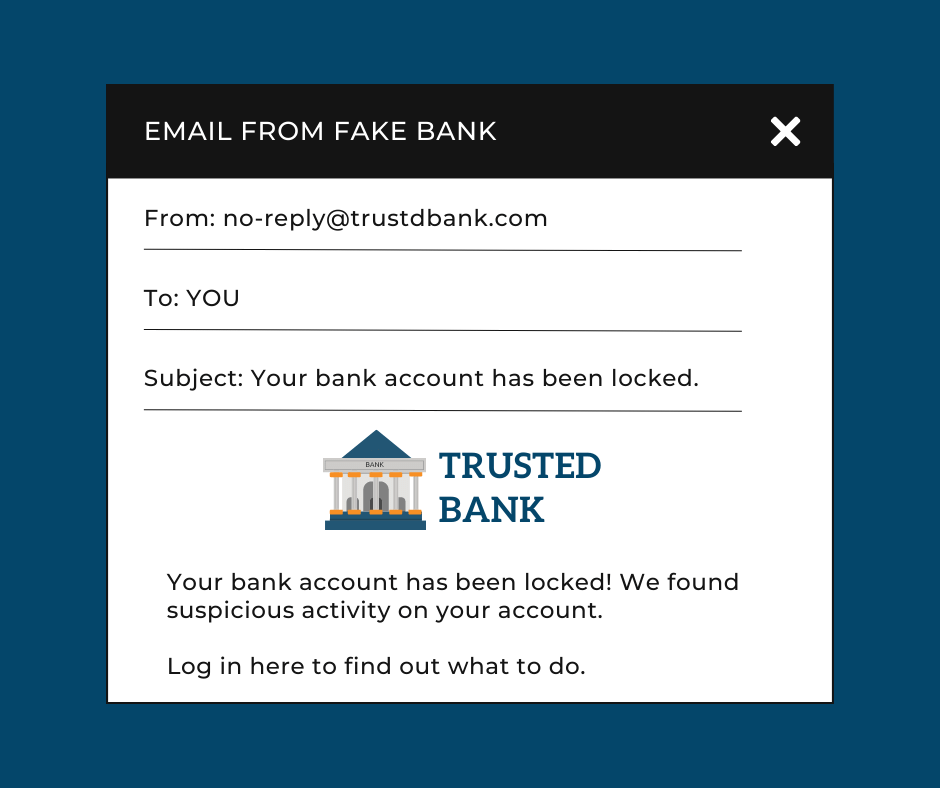
In the context of this article, imagine receiving an email from your bank stating that your account has been locked. It warns you that if you fail to log in to your account, all your money will go to the bank. That’s enough to persuade many to type in their login credentials, which the hackers can now access.
What it Looks Like in Action:
Halo Effect
Most people tend to be more responsive to people or institutions with an established level of authority. These could be government departments, banks, large corporations, or even public figures. That is the halo effect. Hackers abuse that bias by imitating those authority figures and drawing on your trust to create a false sense of security.
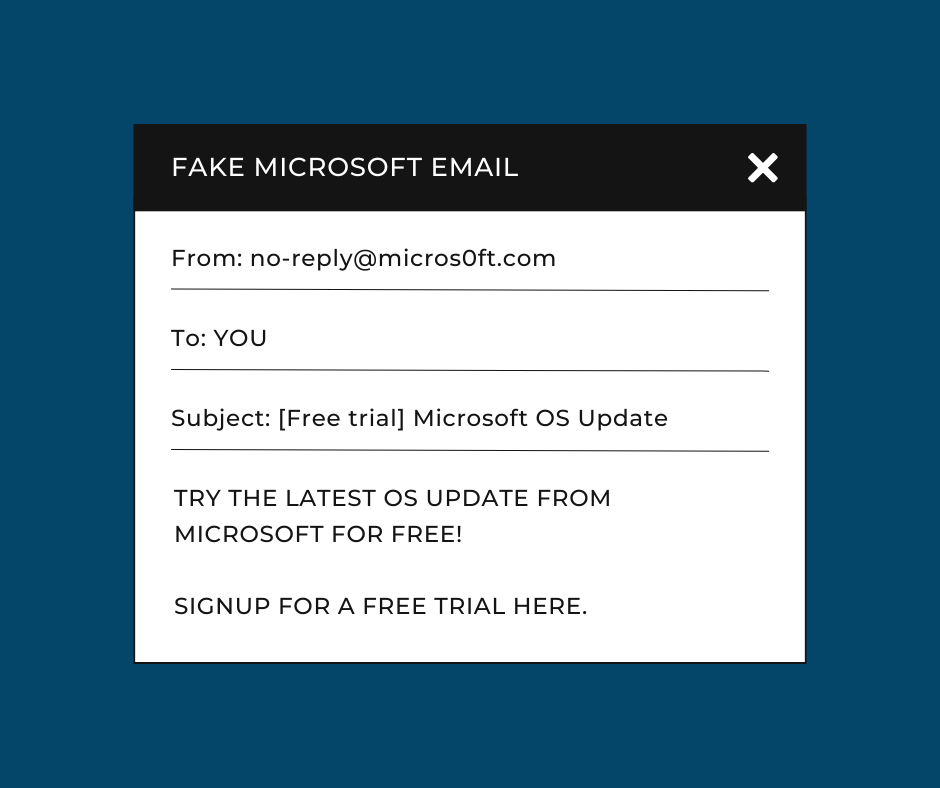
In the example below, a hacker creates an email pretending to be from Microsoft, offering a free trial for their new operating system (OS) if you sign up or download something onto your computer. If the email looks close enough to a real Microsoft email that you’ve received in the past, you'll likely believe it to be trustworthy. However, it might just be a trap laid down by a crafty hacker.
What it Looks Like in Action:
(Email from a hacker pretending to be from Microsoft)
Curiosity Effect
Imagine receiving an anonymous email with a link or attachment that contains tempting information, like payroll for the whole company, etc. Another example says your co-worker is involved in something scandalous, leading you to click a link or attachment for proof. Those are examples of hackers trying to take advantage of the curiosity effect. They want your curiosity to overpower your reasoning, and it can be very effective.
What it Looks Like in Action:
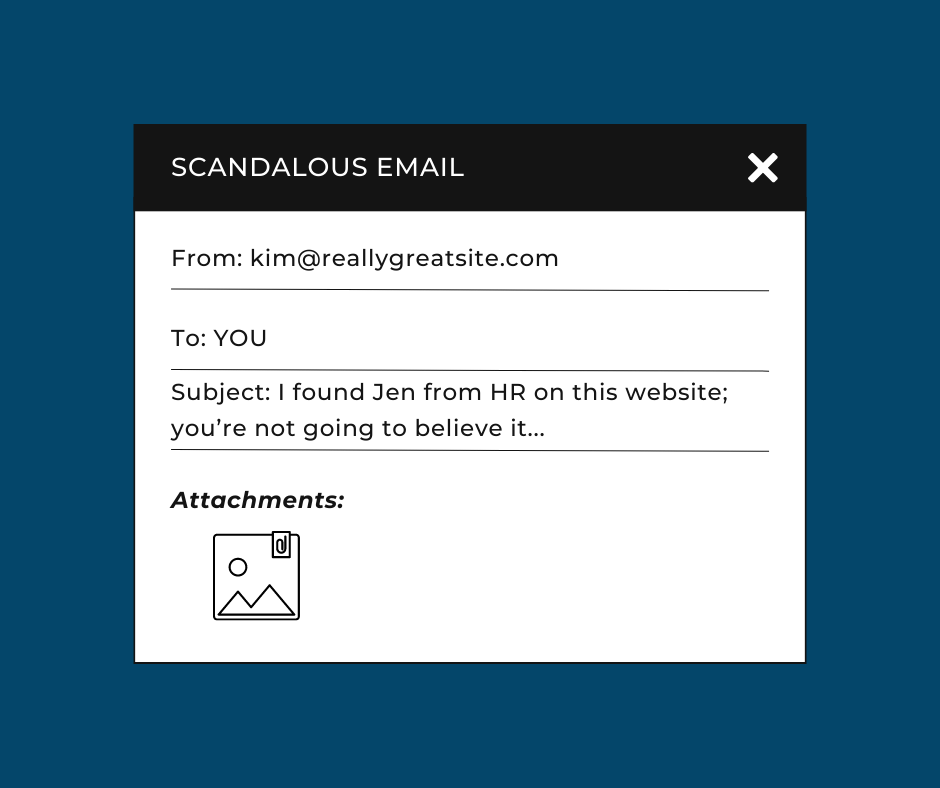
Present Bias
The most basic example of the present bias is the marshmallow test, wherein kids are given a marshmallow and told not to eat it for a certain amount of time. Success would mean they get double the rewards, yet most kids fail within seconds. In short, it’s all about instant gratification. We want our rewards now, not later. Unfortunately, hackers know this all too well, and they use it to help them find easy targets.
What it Looks Like in Action:
Many small businesses would rather forego advanced cybersecurity solutions because it’s an investment that doesn’t generate revenue. For that reason, they would often use their limited resources on other investments that do. Unfortunately, suffering a data breach is often more expensive than investing in cybersecurity in the first place. Hackers know that about small businesses, which is why they often target them.
Ready to Protect Yourself from Hackers?
Unfortunately, there is no tool that can prevent hackers from using your brain against you. The only way to protect yourself from their tricks is to arm yourself and your team with the knowledge of how they are done and what they might look like and share it with everyone. Doing that can improve your chances of avoiding a costly security incident.
ITS has helped hundreds of businesses improve their cybersecurity holistically through advanced solutions and effective security training.
Learn how to train your team to be more vigilant against cyber threats by checking out the resources below:
Mark Sheldon Villanueva has over a decade of experience creating engaging content for companies based in Asia, Australia and North America. He has produced all manner of creative content for small local businesses and large multinational corporations that span a wide variety of industries. Mark also used to work as a content team leader for an award-winning digital marketing agency based in Singapore.
Topics:
