How to Maintain Your Firewall: 5 Best Practices
September 9th, 2022 | 3 min. read

Unhappy with your firewall? You're not alone.
Many organizations feel the same way you do; they aren't doing much except hindering productivity. You've bought the best one available in the market and set it up properly, but data breaches still happen for some reason. It's frustrating. However, before ditching your firewall, you might want to take a closer look at how you're using it first.

In many cases, your firewall just needs proper maintenance to do a better job. It's your first line of defense. It's like a perimeter wall protecting your secure network against unsecured internet. And, like all walls, it needs regular upkeep to do its job of ensuring unwanted traffic stays out.
At ITS, we are a security-focused IT support company dedicated to helping businesses manage and maintain their security tools like firewalls. In this article, we'll share five best practices to help you maintain your firewall to boost its effectiveness.
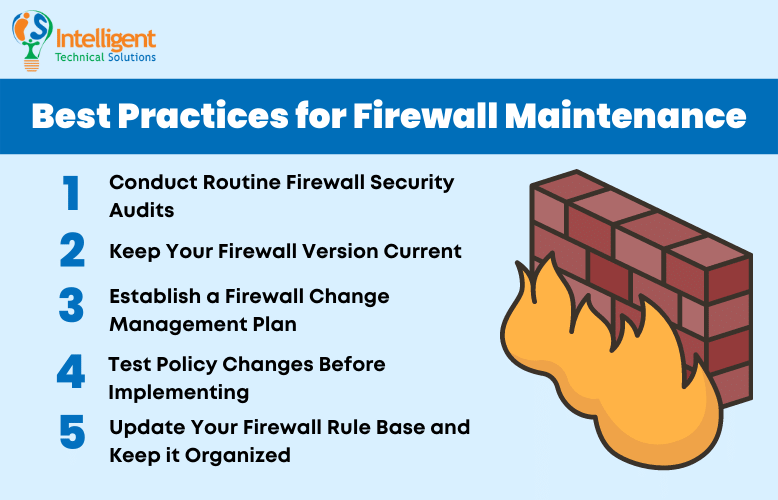
5 Best Practices for Firewall Maintenance
You could buy the best firewall available, but if you're not conducting regular upkeep on it, you're setting yourself up for failure. Firewall maintenance is a vital process that can directly affect how successful it is. It saves both time and money while boosting effectiveness. Check out some of the best practices to maintain your firewall:
1. Conduct Routine Firewall Security Audits
 Regular firewall security audits are essential to help you spot policy violations. Those audits are designed to check if your firewall rules are aligned with organizational security regulations or external compliance requirements. It enables you to stay on top of any policy changes conducted on your firewall that can lead to non-compliance or various other problems.
Regular firewall security audits are essential to help you spot policy violations. Those audits are designed to check if your firewall rules are aligned with organizational security regulations or external compliance requirements. It enables you to stay on top of any policy changes conducted on your firewall that can lead to non-compliance or various other problems.
As a rule of thumb, you should always conduct a firewall security audit every time the following scenarios occur:
- A new firewall is installed
- You are migrating firewalls
- Major configuration changes are carried out
2. Keep Your Firewall Version Current
 Is your firewall up-to-date? If it isn't, you need to consider updating or upgrading quickly. Expired or outdated firewalls carry a lot of risk for your network. In fact, a 2020 survey of 603 US security professionals found that 60% of security leaders believe legacy firewalls don't have the capabilities to protect critical applications and systems from attack. It could lead to serious consequences that leave you vulnerable to all sorts of cyber threats.
Is your firewall up-to-date? If it isn't, you need to consider updating or upgrading quickly. Expired or outdated firewalls carry a lot of risk for your network. In fact, a 2020 survey of 603 US security professionals found that 60% of security leaders believe legacy firewalls don't have the capabilities to protect critical applications and systems from attack. It could lead to serious consequences that leave you vulnerable to all sorts of cyber threats.
Take a look at the following signs your firewall needs an upgrade:
- The firewall uses legacy technology
- The vendor no longer supports the firewall
- Your business needs have changed
3. Establish a Firewall Change Management Plan
 Change is necessary, especially when we're dealing with firewall rules and policies. It ensures that your firewall rules are evolving and are becoming even more reliable in securing and eliminating any risks to your network. However, getting it right requires a high level of preparation. If not, it could lead to bottlenecks and issues that impact your team's productivity.
Change is necessary, especially when we're dealing with firewall rules and policies. It ensures that your firewall rules are evolving and are becoming even more reliable in securing and eliminating any risks to your network. However, getting it right requires a high level of preparation. If not, it could lead to bottlenecks and issues that impact your team's productivity.
Making changes without a plan can lead to loopholes in your network security or issues that impact your team's productivity. Instead, establish a clear, well-defined, and complete firewall change management plan before moving forward. To give you an idea of what that looks like, take a look at what it should consist of:
- A full list of changes and their objectives
- An overview of estimated risks as a result of the policy changes, how they can impact the organization, and how to mitigate them
- Information on who is responsible for the change, when it will be put in place, the reasons for the change, and the results
- A centralized workflow detailing the management and control of the change and policy
4. Test Policy Changes Before Implementing
 Test the consequences of a policy or rule change before implementing them across your network. That could help prevent any undesired effects like network traffic disruptions, poor firewall performance, etc. To do that, work in a test environment first. From there, you can observe how the changes will affect the environment before implementing them on your actual system.
Test the consequences of a policy or rule change before implementing them across your network. That could help prevent any undesired effects like network traffic disruptions, poor firewall performance, etc. To do that, work in a test environment first. From there, you can observe how the changes will affect the environment before implementing them on your actual system.
5. Update Your Firewall Rule Base and Keep it Organized
 As we've mentioned above, change is necessary with firewall policies. However, equally as important is keeping track of policy changes and organizing them. Cleaning up your firewall rule base is essential to optimizing it. Otherwise, it could sow chaos and confusion caused by an abundance of firewall rules, such as redundancies, duplicate rules, or bloated rules.
As we've mentioned above, change is necessary with firewall policies. However, equally as important is keeping track of policy changes and organizing them. Cleaning up your firewall rule base is essential to optimizing it. Otherwise, it could sow chaos and confusion caused by an abundance of firewall rules, such as redundancies, duplicate rules, or bloated rules.
To avoid that outcome, you need to ensure all unnecessary rules are removed and the ones that you do need are optimized and maintained properly.
Ready to Conduct Firewall Maintenance?
Before opting for a different firewall, check if you're conducting proper maintenance first. Regular upkeep of your firewall can help save you time and money while boosting its effectiveness. If you follow the best practices below, you will definitely see improvement in how your firewall performs in the future:
- Conduct routine firewall security audits
- Update and keep it current
- Establish a policy change management plan
- Test policy changes before implementing them
- Update your firewall rule base and keep it organized
At ITS, we are dedicated to helping businesses make the most of their firewalls and other technology. Check out our video on why firewalls fail and how to prevent them. After reading, you’ll learn about the best practices for keeping firewalls in working order, helping your business make the most of the technology.
Mark Sheldon Villanueva has over a decade of experience creating engaging content for companies based in Asia, Australia and North America. He has produced all manner of creative content for small local businesses and large multinational corporations that span a wide variety of industries. Mark also used to work as a content team leader for an award-winning digital marketing agency based in Singapore.
Topics:
